Securing hardware is essential to keep confidential information secure against malicious entities since all the running applications interact with the underlying hardware. Any vulnerability in a hardware design may lead to information leakage, which needs to be detected and fixed before it is exploited. Several faculty members have ongoing projects exploring hardware vulnerabilities and how to make a hardware design more secure against third-party attacks.
Countering Power Analysis Attacks Using Reliable and Aggressive Designs: Random dynamic voltage frequency scaling (RDVFS) has been proposed to prevent side-channel attacks using differential power analysis (DPA) and correlation power analysis (CPA). However, due to the one-to-one mapping present between the voltage and frequency of DVFS voltage-frequency pairs, RDVFS cannot prevent power attacks. We have developed a novel countermeasure that uses reliable and aggressive designs to break this one-to-one mapping correlation significantly, one order of magnitude. For more information related to this and other research, visit: https://www.engineering.iastate.edu/directory/profile/arun
Side-channel Attacks: Dr. Akhilesh Tyagi’s research focuses on discovering new vulnerabilities by leveraging power consumption and electromagnetic signals during the software execution. The information collected from these signals may lead to cryptographic key leakage. For more information visit: https://www.engineering.iastate.edu/directory/profile/tyagi
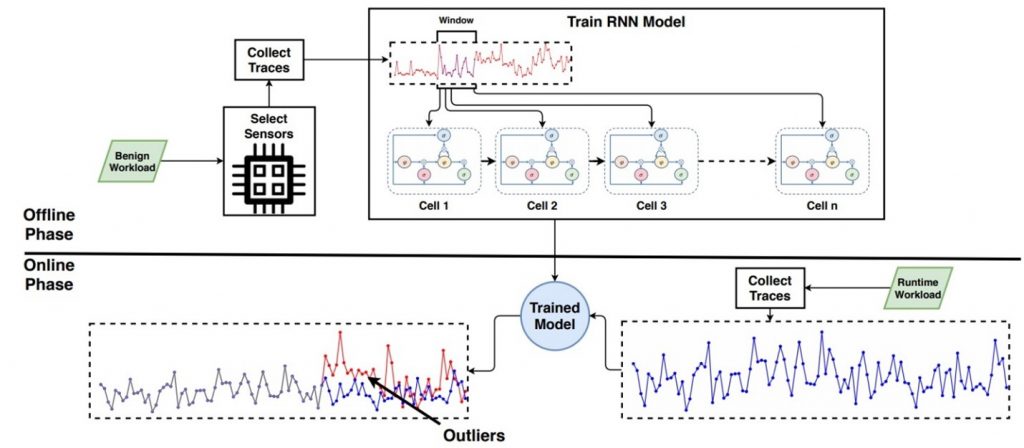
Microarchitectural Attacks: Intel, AMD, and ARM chips are the core components that execute instructions. While many optimizations were introduced to increase the computation power of the chips, several hardware and OS features can be exploited to leak confidential information. Dr. Berk Gulmezoglu’s research lab focuses on the discovery of unexplored vulnerabilities in the chip designs as well as anomaly detection with Deep Learning algorithms. For more information visit: https://www.ece.iastate.edu/bgulmez/